Nicolas Krassas is a member of the Synack Red Team and has earned distinctions such as SRT Envoy and Guardian of Trust.
A few days back, there was a release of a Synack target where one of the systems had an open to internet squid proxy running on port 3128. Normally we report the access control issue and we stop further actions, but this time Synack’s Vulnerability Operations team needed to provide a bit more impact for the client. Time to deliver impact!
What is an open proxy?
An “open to the internet proxy” or “open proxy” typically refers to a proxy server that is accessible from the public internet and not restricted in who can use it. A proxy server is a server that acts as an intermediary between a client (e.g., a user’s computer) and a target server (e.g., a website). It can be used for various purposes, including enhancing security, privacy, and performance. When you use a proxy server like Squid, you route your internet traffic through it, and the proxy server then forwards your requests to the destination server on your behalf.
Here’s how it works:
- A user sends a request to the open proxy server.
- The proxy server receives the request.
- The proxy server forwards the request to the target server (e.g., a website).
- The target server responds to the request.
- The proxy server receives the response from the target server.
- The proxy server sends the response back to the user.
What is often not taken into consideration is that the proxy will work both ways on the default setup, that means the proxy will “proxy traffic” toward the internet but also toward internal systems.
To access the internal network, we need to know the internal IP addresses that are used. The range of IP addresses is large, so we tried to figure out an alternative method.
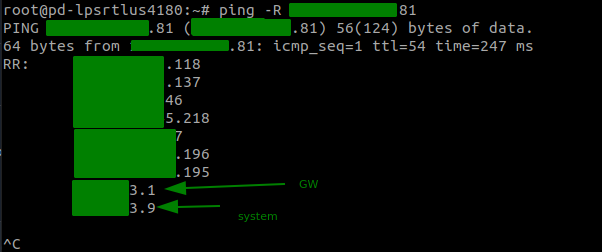
Ping to the rescue!
One possibility, that not many know about, is to use the ping command, which can also provide a routing path. Specifically, the record route (-R) is a great option, where traceroute will not provide further information.
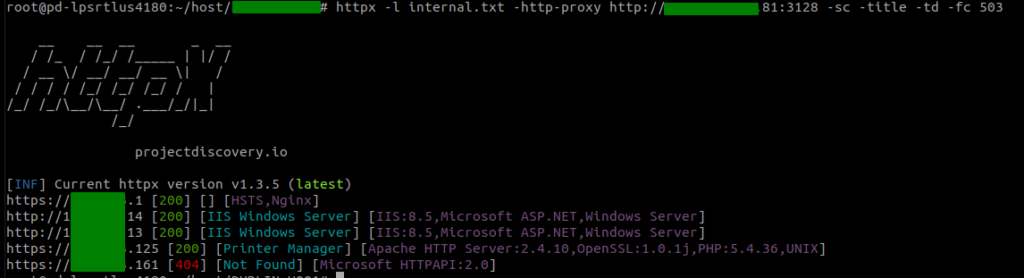
With the knowledge of the internal network, we proceeded in creating a list of all network addresses in a file and passing this to our httpx with a parameter to use the proxy server as well.
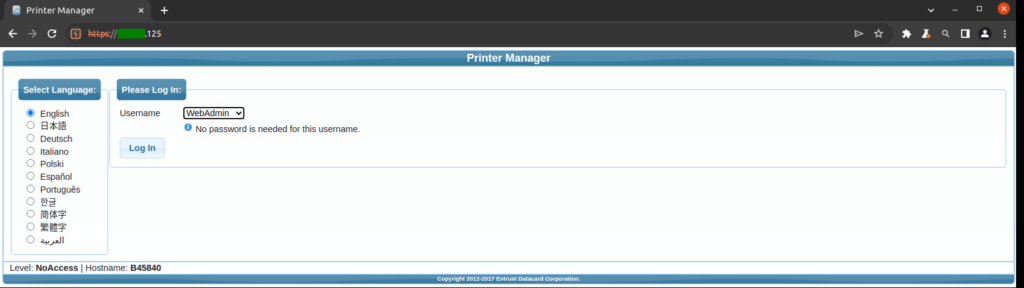
With the retrieved information, and by configuring our browser to use the proxy, we were able to gain access to go further into the environment, where, for demonstration purposes, we proceeded into accessing the Printer Manager page, which allowed administrator access without any password.
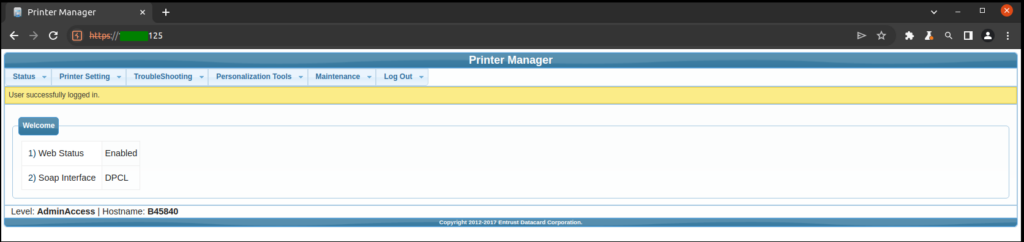
And, we’re in!
Recommendations to prevent an open proxy attack
These are a few methods you can employ to keep proxy servers more secure.
- Implement access controls: Limit who can use the proxy server by using access controls, such as IP whitelists, authentication, or other security measures.
- Monitor and log proxy traffic: Regularly review logs for suspicious activities and unauthorized use.
- Keep software up to date: Ensure that the proxy server software is patched and updated to prevent known vulnerabilities.
- Employ content filtering: Implement content filtering to block access to malicious or undesirable websites.
- Educate users: Raise awareness among users about the risks of using open proxies and discourage their use for malicious purposes




