Synack PTaaS
Platform
An end-to-end security testing solution to find and
remediate the vulnerabilities that matter and improve
your security posture over time
One platform, many uses.
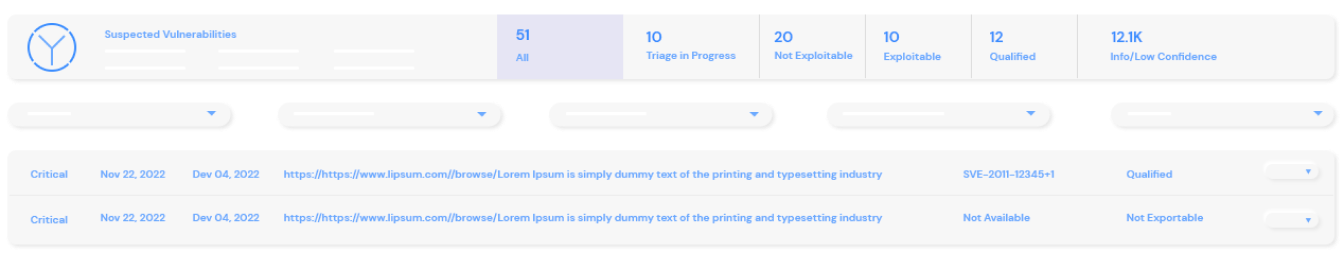
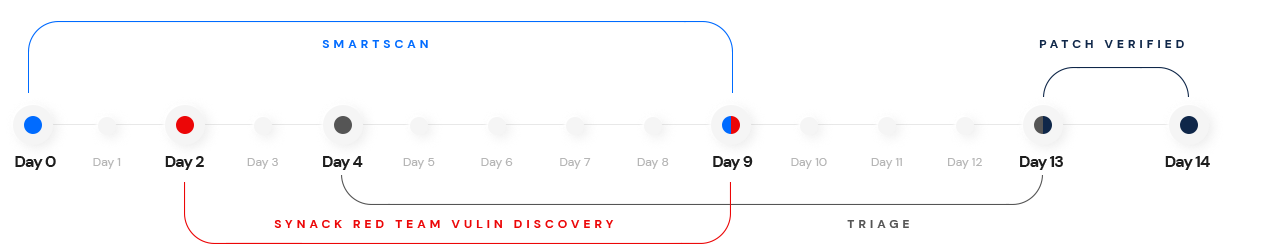
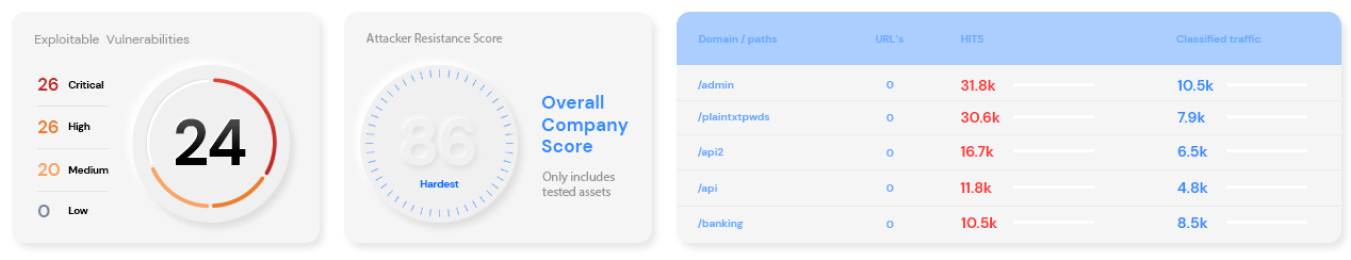
Expect a Penetration Testing as a Service (PTaaS) platform that provides full control and visibility of the attack surface, reveals patterns and deficiencies in your security program, enables organizations to take action on critical vulnerabilities and provides executive-level reporting for leadership and the board of directors.