Benefits
Identify, Assess and Remediate with Continuous Vulnerability Management
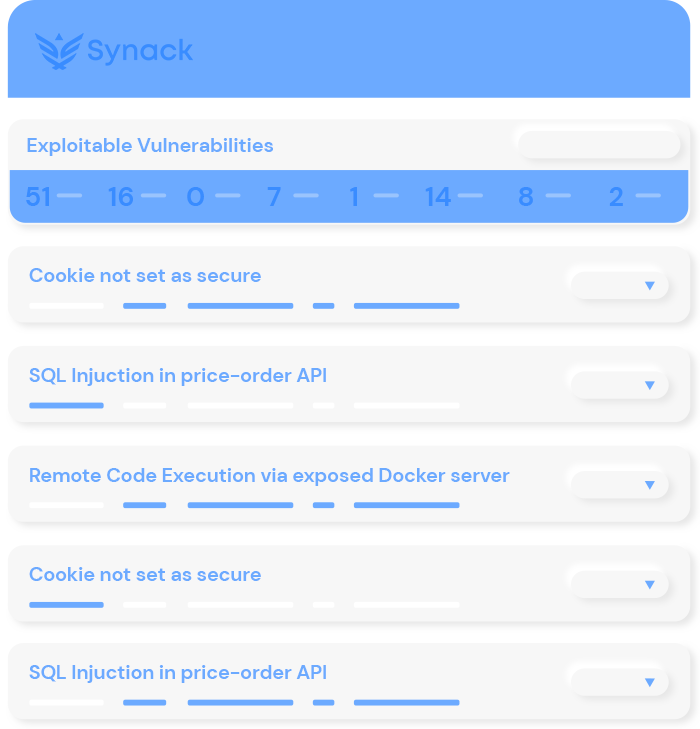
Find Exploitable Vulnerabilities
Unlike automated noisy vulnerability scanners,
Synack continuously evaluates and prioritizes the most critical and exploitable vulnerabilities so you don’t have to.
Actionable Metrics
See total amount of vulnerabilities found, get analysis on which are the most severe, review stats from the testing performed and receive patch efficacy data.
Integrations
Consolidate your vulnerability management process through your existing tools, such as ServiceNow and JIRA, through integrations.
Vulnerability Management with Patch Verification and Convenient Workflows
1
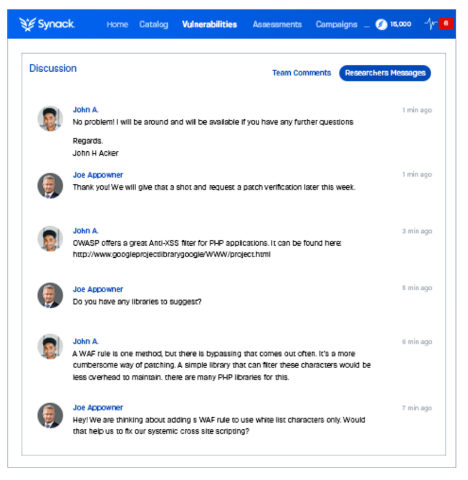
Real Time Vulnerability Analytics
2
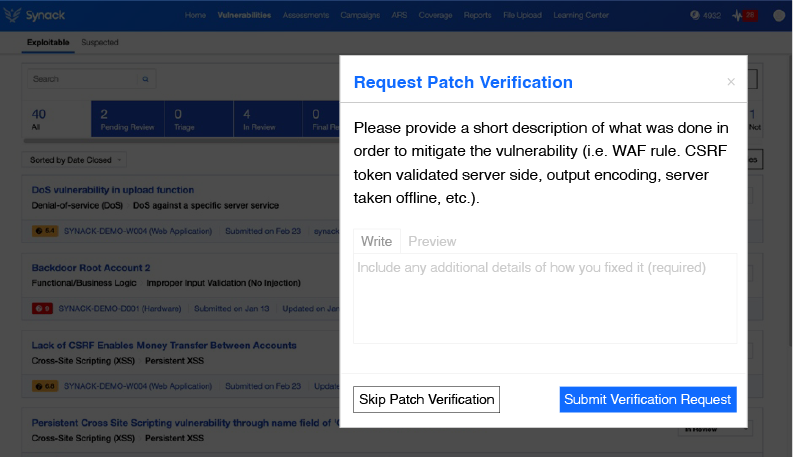
On-demand Patch Verification
3
Vulnerability Assessment and Replication
4
Integration with Existing Tools
FAQ