Security Testing
Frameworks We Meet







Achieve Risk Management and Compliance with Synack Pentesting
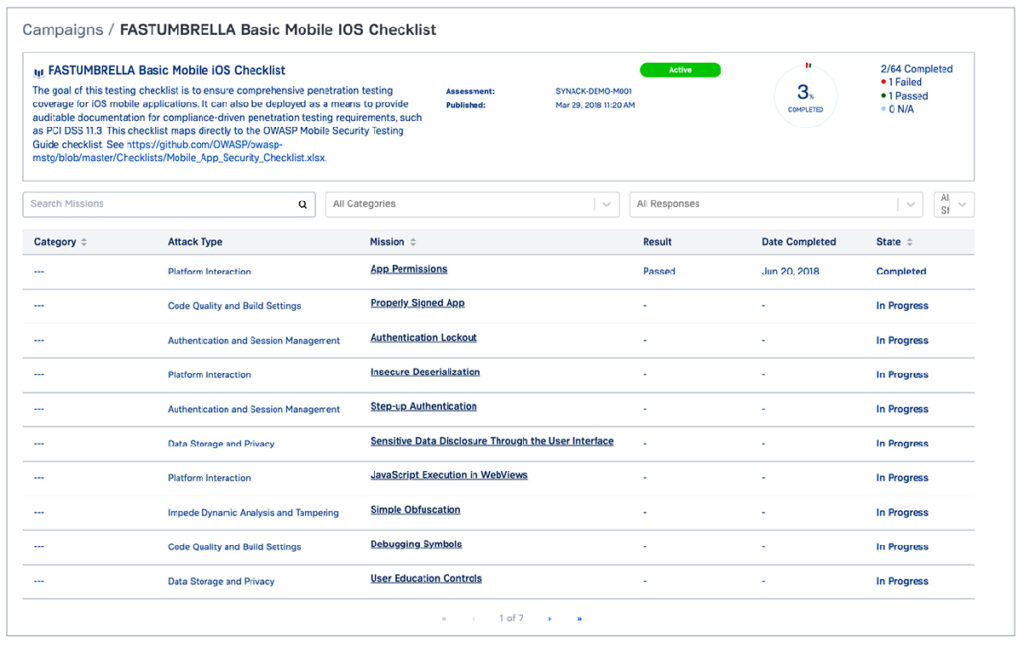
Synack Missions: Fast and On-demand Security Checks
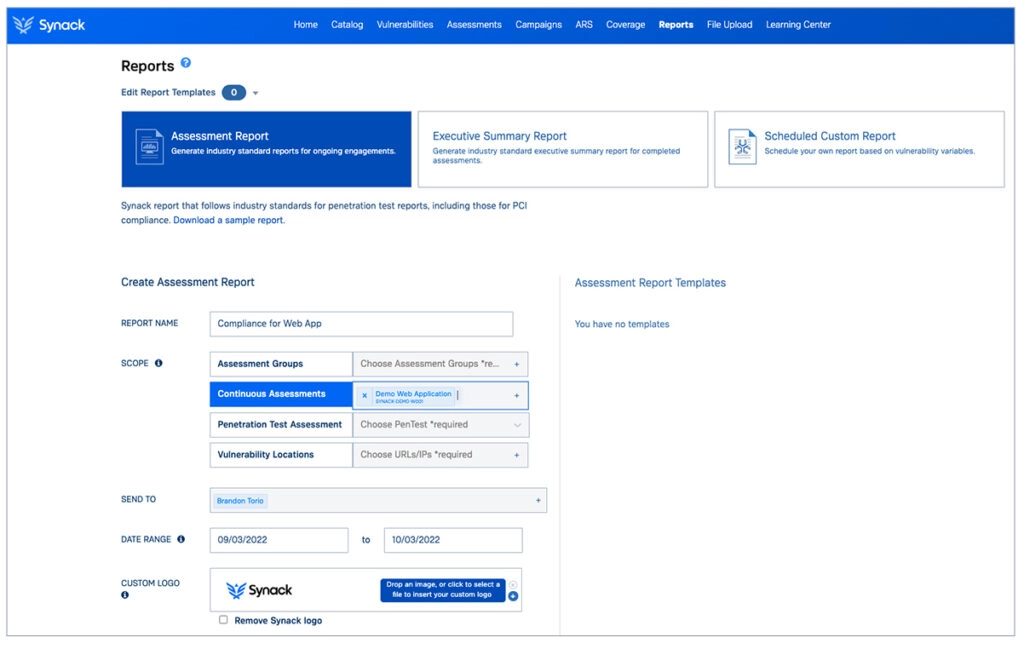
Report Generation with Proof-of-work
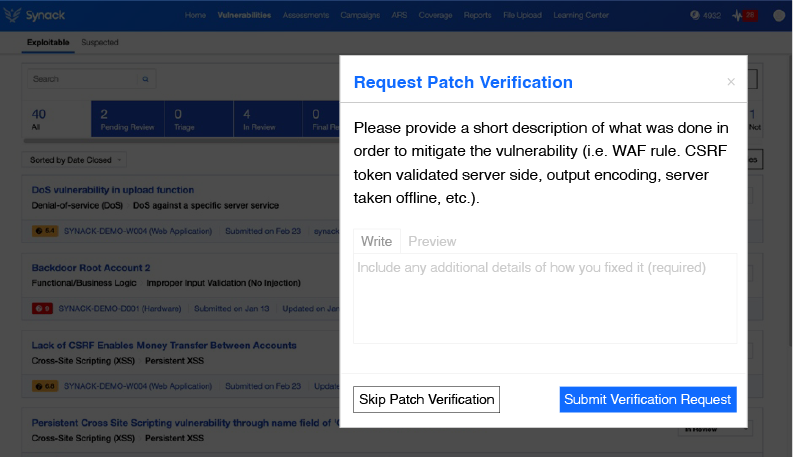
Real-Time Reporting and Patch Verification to Speed Up Remediation
Synack14 Pentest
Many regulatory frameworks require a security assessment which can be met with Synack14, a 14-day pentest that utilizes incentive-driven testing conducted by a diverse community of highly-vetted researchers to discover exploitable vulnerabilities.
Continuous Pentesting
Go beyond compliance to minimize risk and harden your attack surface with Synack365 and Synack90, which blends automatic and adversarial human analysis with the Platform’s vulnerability management to maximize efficiency on a continuous cadence.
On-demand Security Tasks
Through the Synack Catalog, SRT researchers can be activated to run vulnerability checklists like OWASP Top 10 and NIST 800-53, document their work, and generate reports to demonstrate adherence to regulatory standards and security controls.