Putting the Most Critical Vulnerabilities First
Vulnerability testing, whether via an automatic scanning program or human-based penetration testing, can find an overwhelming number of vulnerabilities in your system as recent trends would suggest. Since 2017, record numbers of Common Vulnerabilities and Exposures (CVEs) have been reported, with 2022 on track to set a new high.
Sorting through a record number of vulnerabilities to keep your organization secure is a daunting task without additional support and distillation.
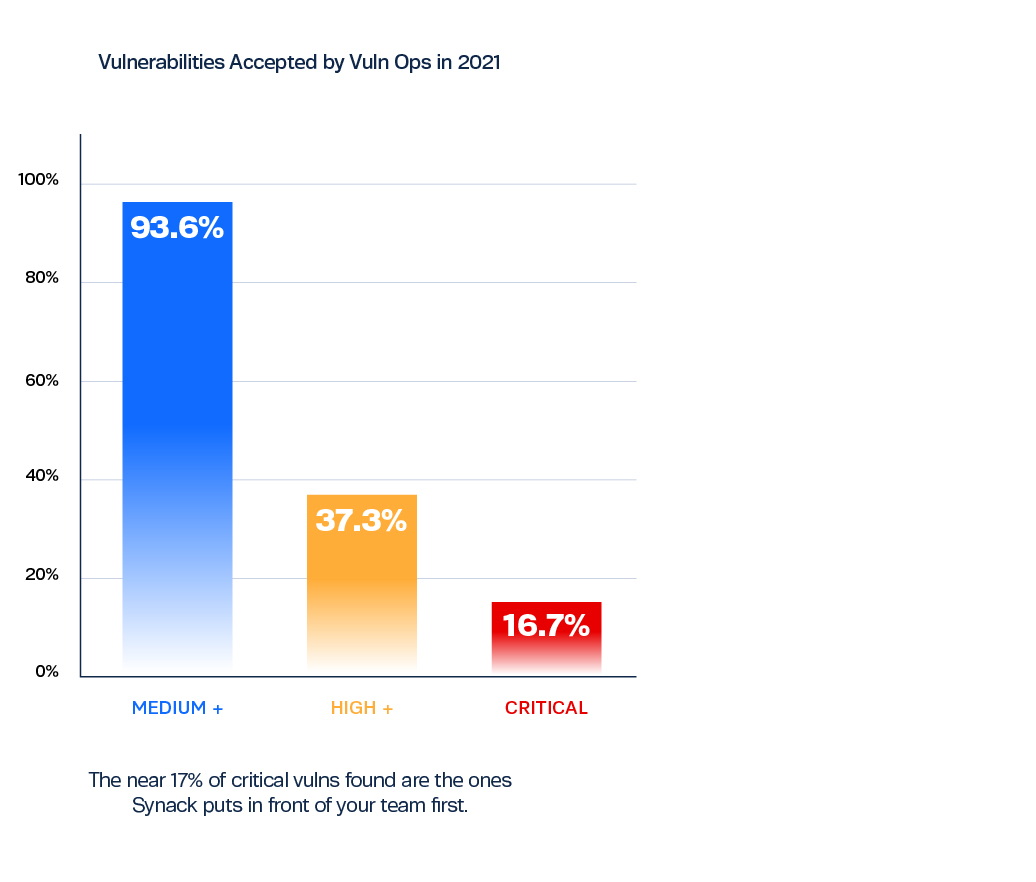
The good news is that of all the vulnerabilities that might show up on a traditional vulnerability report, only around 5% of vulnerabilities discovered are ever exploited in the wild. And most of the exploited vulnerabilities are those with the highest CVSS (Common Vulnerability Scoring System) severity score of 9 or 10.
So how do you know which vulnerabilities in your system need to be addressed right now, and which can be put on the back burner? Some vulnerabilities are an immediate risk to the business, while others are highly unlikely to be exploited. Prioritizing critical vulnerabilities can mean the difference between preventing an attack and responding to one.
Finding and triaging critical vulnerabilities is where Synack’s pentesting outperforms traditional models. We continuously prioritize impactful vulns for your organization, surfacing only vulnerabilities that are reproducible and show exploitability.
The Synack Difference—The Vulnerability Operations Team
The Synack Platform is the only solution to harness the best in augmented intelligence for more effective, continuous pentesting. First, the Synack Red Team (SRT), a group of vetted researchers, conducts open vulnerability discovery, while our automated SmartScan® provides broad attack surface coverage. Together, they find vulnerabilities across your attack surface.
Next, the Synack Vulnerability Operations team assesses vulnerabilities found by the SRT and SmartScan by using a rigorous vetting process. Noise, such as duplicate submissions by SRT or non-replicable exploits, low-impact vulns, is kept to a minimum during penetration testing and you’re ultimately served vulnerabilities that present a clear risk.
This additional step to triaging is key to faster remediation and minimizing business risk.
The Vulnerability Operations team is a group of seasoned security professionals with hacking expertise. They are full-time Synack employees with extensive vulnerability knowledge–they’ve seen tens of thousands of them. For the most accurate triaging, high impact vulnerabilities are often reviewed by multiple team members. So, when you get a vulnerability report from Synack, you know that it matters.
Remediating Exploitable Vulnerabilities with True Business Impact
The Vulnerability Ops team works alongside the SRT 365 days a year to bring order to the thousands of CVEs. When the team receives an initial vulnerability report, they will first validate the vulnerability by replicating it based on details provided in the report. When the vulnerability is confirmed, the Ops team proofreads and formats the report for utility and readability by a development team. Everything needed to reproduce the vulnerability is provided in each report.
After vulnerabilities are deemed exploitable and impactful, and the report has been detailed with steps to reproduce and suggestions on remediation, it will be published to the Synack Platform.
From there, the Synack Platform provides real-time findings on vulnerabilities found–their CVSS score, steps to remediate and evidence of the researcher’s finding. With this information you can address the vulnerabilities that are most important to your organization in a systematic and thorough manner.
Through the Synack Platform, teams are also able to check if their remediation efforts were successful with Patch Verification. Patch Verification can be requested on-demand, and the researcher will provide further communications on the patch efficacy.
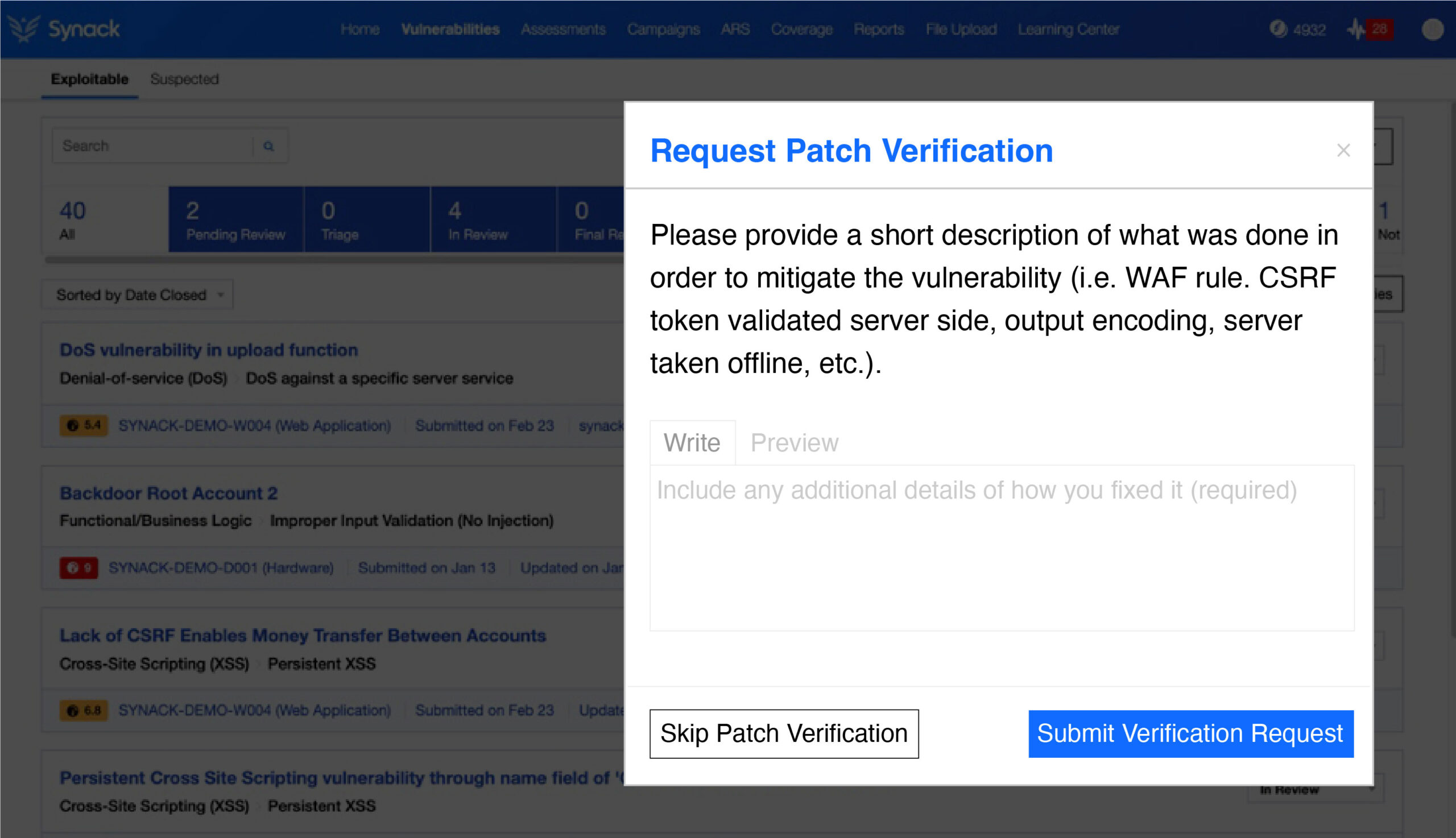
The Synack Platform facilitates delivery of vulnerabilities and
actions like submitting patch verification requests.
2021 Vulnerability Highlights
The six most popular types of vulnerabilities delivered to organizations were:
- Cross-site Request Forgery (XSRF)
- Authentication Permission
- Information Disclosure
- SQL Injection (SQLi)
- Functional Business Logic
- Authentication Session
Making the Most of Vulnerability Testing
Most organizations don’t have the resources to go chasing every vulnerability reported from initial testing. To further safeguard your organization, someone needs to determine which are true vulnerabilities and which of those are exploitable and at what level of criticality. That process is noise reduction, and it is essential for any cybersecurity operation to shoot for the highest level of noise reduction before proceeding to remediation. Synack, through the Vulnerability Operations, team can take on this task for you.
Using Synack’s unique approach to continuous pentesting, your team will be able to proceed with confidence that their remediation efforts are critical to keeping the organization secure. Get started with Synack penetration testing today.