Traditional Pentesting Is a Static Solution To a Dynamic Problem
Recently, Microsoft disclosed four zero-day vulnerabilities in Microsoft Exchange Servers. A Research Director from Palo Alto Networks claimed that adversaries were scanning for vulnerabilities within 25 minutes of vulnerabilities being released. Synack customers discovered the critical Apache Log4j vulnerability (CVE-2021-44228) within hours of its disclosure through a Synack CVE check offering. Scanning traffic for the vulnerability piqued just five days after the disclosure and has continued. There has never been a higher need for fast reporting and remediation timelines on high-priority vulnerabilities.
In the 1970s, James P. Anderson invented point-in-time pentests as a public policy and technical innovation to secure communication systems and other networks from malicious hackers. But the threat landscape and the sophistication of digital threats have changed vastly since then, having a significant impact on pentesting. Other major factors include increased attacker sophistication and vulnerabilities, new DevSecOps workflows and collaboration/security software (Splunk, Jira, Slack, SOAR, etc.), and growing adoption of cloud services, infrastructure, and storage. With these macro changes, the traditional way of doing pentesting is too slow, disruptive, and ineffective. The good news is that Synack has heard these customer challenges and developed an on-demand pentest that’s continuous, performance-driven, and intelligent.
Cloud Services & Providers Are Dynamic
Point-in-time pentesting cannot keep pace with agile cloud services, which are often spun up around specific projects. On average, large organizations add 3.5 new publicly accessible cloud services per day. Remote code vulnerabilities or external misconfigurations can occur at any time and leave organizations’ public and private assets vulnerable.
New DevSecOps Workflows & Security Software Stack
The average security team now uses about 45 cybersecurity-related tools on their network. Collaboration tools have replaced email. Typically, most security, ops, and development teams communicate using Splunk, Slack, Jira, or ServiceNow. Code releases are constant. It’s important to have a DevSecOps process that automates a lot of the work across these platforms, or risk spending time on administrative processes that distract from securing your organization.
Increase In Sheer Number of Vulnerabilities & More Sophisticated Adversaries
Security researchers have found an increasing number of vulnerabilities in recent years. In fact, the number of new vulnerabilities increased by 127% from 2017-2018 compared to single digit growth rates in previous years. An average of roughly 17,416 new vulnerabilities are added each year and point in time pentests can’t keep up. Attackers are more efficient than ever with some popular exploitable vulnerabilities pursued within a hours of when a patch is released (i.e. Microsoft Exchange CVE-2021-26855, Apache Log4j CVE-2021-44228)
What Pentesting Challenges Are Security Leaders Facing Today?
Speed
Typically, in a traditional pentest model an organization seeks out an established consulting firm to do the work. As the complexity of assets has increased, pentesters specialize; they vary in attack types (reverse engineering, password cracking, etc.), and focus on certain asset types (IoT, mobile, web, IaaS). Hiring enough skilled personnel is a top challenge to implementing and maintaining a pentest program. As a result, pentesters with sought-after skill sets may need to be scheduled months in advance. Scheduling a new program, or launching a new test can take weeks or even months, especially if the team needs to work on site.
Disruption
Too often, security teams do not receive sufficient support to effectively communicate results. Vendors send pentest reports in PDFs or Excel via email. A security team member needs to copy and paste information into ticketing tools like Jira or ServiceNow, or collaboration tools (i.e. Slack). Reports are written in a way that’s not accessible to other key teams like legal, operations, IT or development. If they have questions, security teams can’t easily communicate with researchers that surface the vulnerabilities. Finally, once a vulnerability is closed, it’s not possible to re-test the vulnerability in a standard pentest. Vulnerabilities can fall between the cracks and take months or years to remediate.
Effectiveness
One of the most frustrating aspects of penetration testing is the inability to see meaningful progress over time. How can you create a benchmark for your defenses? What security metrics should you consider to take stock of your various assets besides the CVSS score or quantity of vulnerabilities? Traditional pentesting does not provide holistic risk scores at the asset or company level.
In response to these challenges, Synack offers a continuous, intelligent, and performance-driven on-demand pentest to improve your organization’s security posture overtime.
Synack Provides a Better Way to Pentest
Harness the Best Talent Globally On-Demand
More than 1,500 vetted security researchers from across the globe are actively working with the Synack Red Team, hunting for vulnerabilities around the clock. The SRT is second to none when it comes to skills and trust, thanks to rigorous vetting and assessment of researcher expertise in the application process. Synack Ops can launch new pentests in as little as 3–5 days and start on-demand security tasks such as asset discovery in seconds.
Test for Cloud Misconfigurations, New Vulnerabilities, and Dynamic Host Changes
Organizations need to be wary of new vulnerabilities like Log4J or SolarWinds Orion. It’s never been more important to continually test public and private cloud assets. Synack offers configuration reviews of Azure environments, CVE checks, and testing for dynamic internal and external hosts. Synack integrates with numerous cloud providers (AWS, Azure and GCP). Additionally, our API pulls from major cloud providers daily to help detect any changes to external hosts when Synack is testing.
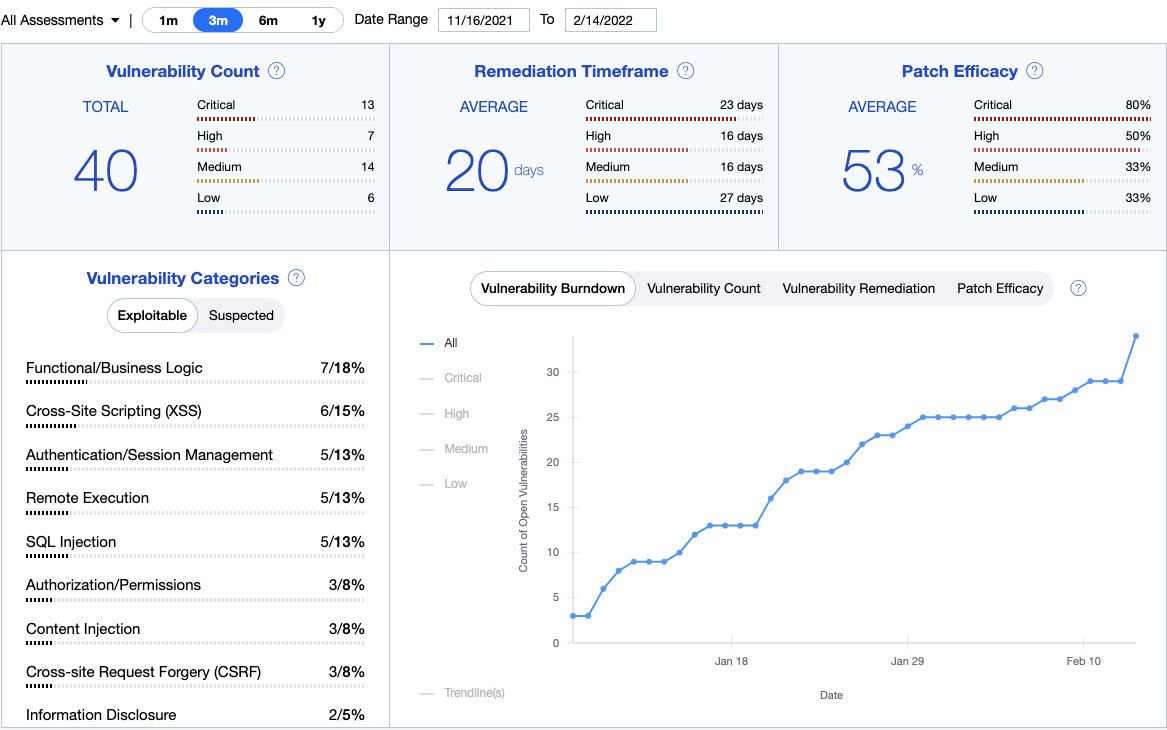
Measure Performance Overtime with Metrics on Remediation, Patch Efficacy, and Risk Scoring
With traditional pentesting, there are not a lot of great metrics for measuring your security status overtime. Number of vulnerabilities found can be a helpful benchmark, but often don’t include other critical stats such as vulnerability remediation timelines. Synack provides a security risk score that takes a holistic approach based on metrics like attacker cost, severity of findings, and remediation efficiency.
Scale Testing with a Technology Platform
Synack offers 43% more coverage of your assets than a traditional pentest with SmartScan, a scanner that you can use on your medium priority assets to surface vulnerabilities. These “suspected vulnerabilities” are triaged by the researchers in order to provide you with actionable results.
Compliance (PCI-DSS, FISMA, HIPAA) Ready Reports & Actionable Results
Traditional pentests are built for your organization’s compliance objectives, but lack the agility necessary for digital transformation. Synack provides easily readable and compliance-ready reports on a wide range of metrics (i.e. vulnerability severity, vulnerability status, steps to reproduce, recommended fixes, remediation status) for legal, policy and leadership teams as well as real-time metrics on exploitable vulnerabilities that are the top priority for security, ops and development teams. Synack also integrates with Jira, ServiceNow, Splunk, and offers an API to facilitate faster DevSecOps processes.
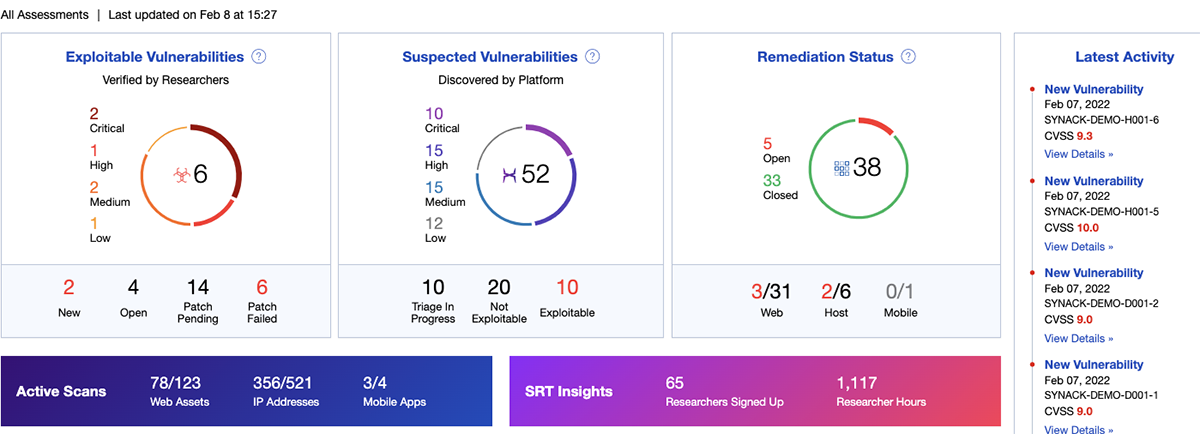
Attackers are more vigilant than ever. Security teams need to be one step ahead of their adversaries to help make sure they are keeping their organizations’ environments safe. The choice is clear. Synack provides 159% more ROI than a traditional pentest.
Change your pentest provider today and schedule a demo with our team, or download a solutions overview of Synack 365—our continuous pentest offering.




