Reduce risk to third party partners and M&A targets
An estimated 82% of CIOs believe their software supply chain is vulnerable (Venafi, 2022). The reality is that their attack surface is your attack surface. The implications of not conducting due diligence are serious. An unknown data breach could impact the value of an acquisition, or an exploitable vulnerability in a supplier could lead to loss of intellectual property, or damage your brand. It’s better to know what you don’t know.
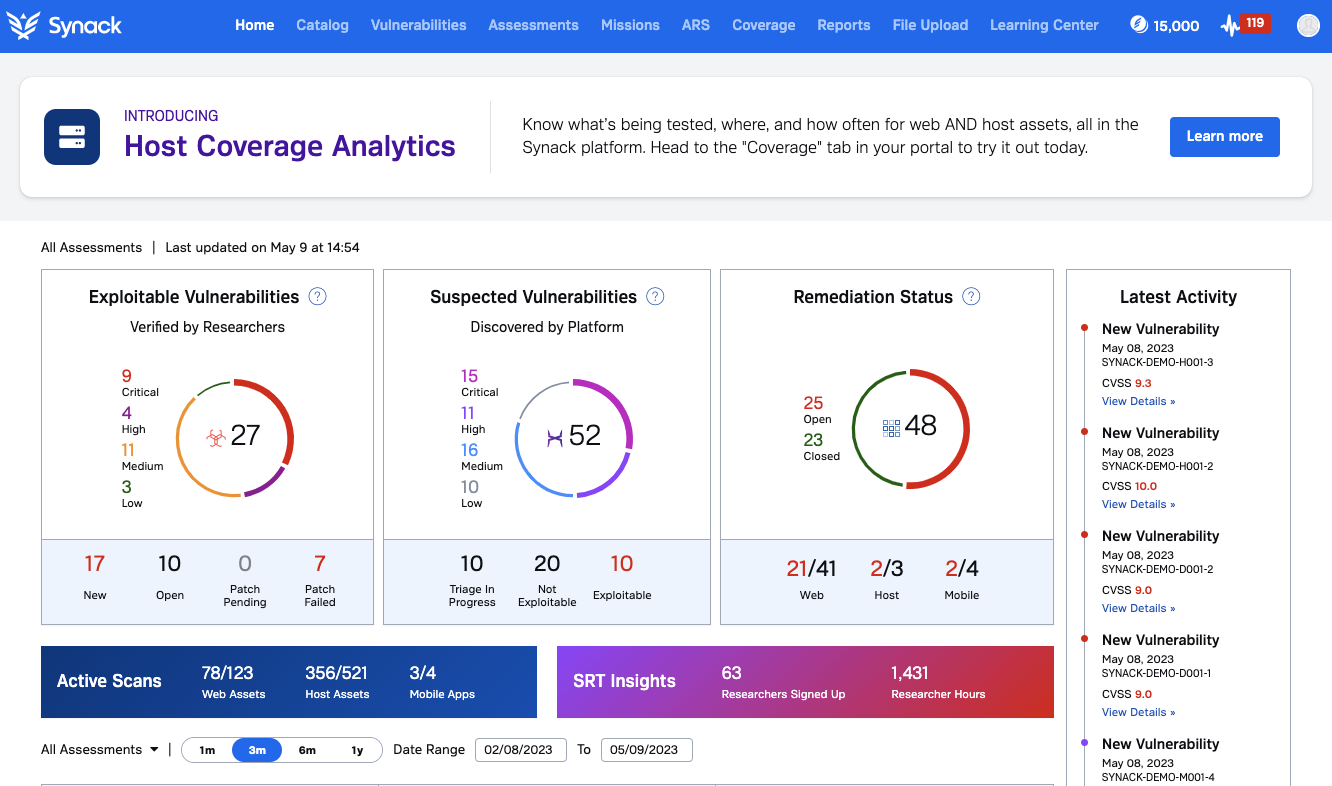
Vulnerability Management
Discover, validate, re-test, and track remediation of vulnerabilities in a single platform.
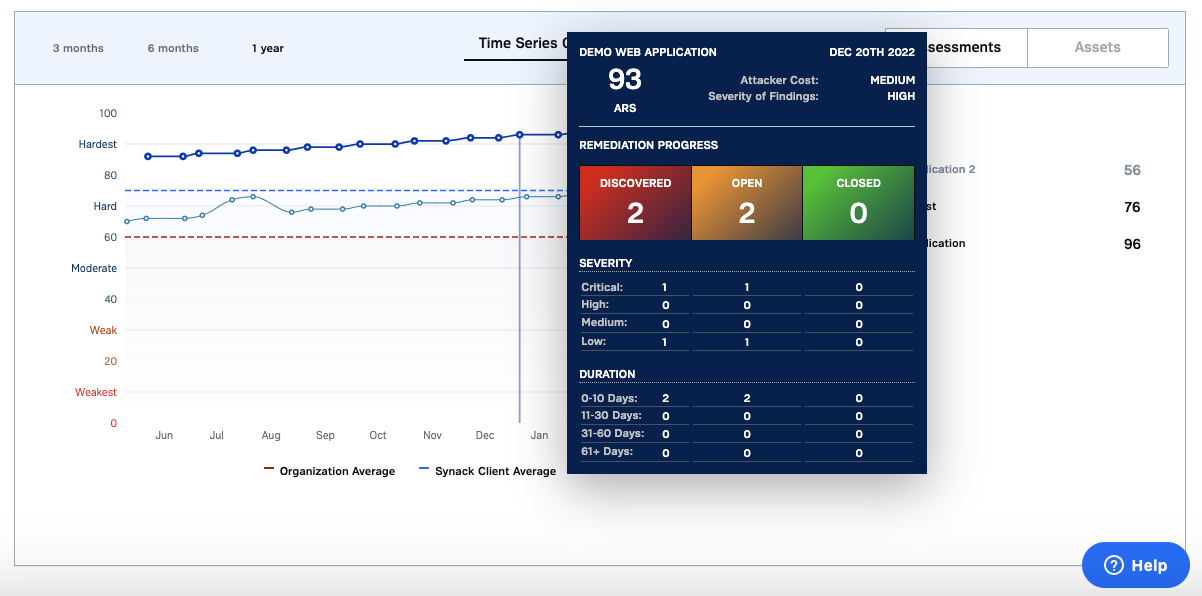
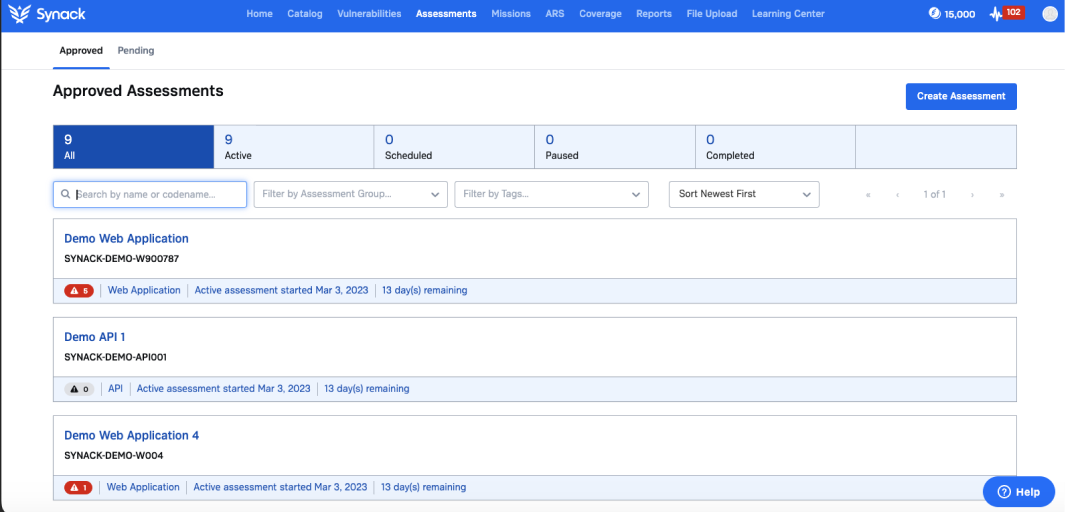
Easy On-Demand Testing
Choose from a variety of testing methodologies (OWASP, NIST, Open Vulnerability Discovery) and launch tests at the click of a button.
Third Party Risk Visibility
Synack provides a risk score across all assets and assessments. Get an offensive perspective on which third parties are susceptible to attack.
Synack provides a strategic option for third party risk assessments