Why You Need to Think Strategically
It’s no great revelation that tactics, techniques, and procedures utilized by nefarious hackers hacking activities are evolving on a daily basis. In 2022, 18,828 common vulnerabilities and exposures (CVEs) were published. At the same time, organization attack surfaces are expanding. The average large enterprise attack surface encompasses 8,500 IPs. It has never been more challenging to keep your attack surface secure, and your current pentesting program likely won’t help you get there.
So how do you use your limited security staff and budget to find, prioritize and remediate vulnerabilities across your expanding attack surface? The answer is adopting a risk-driven, rather than compliance-driven, approach that leverages strategic and tactical approaches to pentesting. The Synack Platform core components of vulnerability management, operations and support, an API and integrations, reporting and real-time analytics, and managed community provide the testing and data necessary to make progress in securing your attack surface and satisfy compliance requirements.
Developing an Ideal Security Testing Strategy
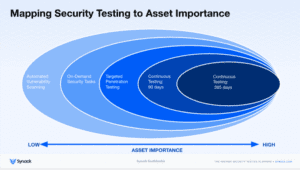
Testing needs to be performed on assets across your entire attack surface, deploying testing based on asset’s risk value or its proximity to sensitive data. You may want to deploy continuous penetration testing for high-value or high-risk assets and deploy automated scanning on lower value or low-risk assets. Asset test history should maintain records not only of tests performed, but also results and timing so that testing can be analyzed over time and across security programs. Applying this methodology, remediations can have a system-wide effect when solving for the root cause of an issue.
>> DOWNLOAD: The Guide to Strategic Security Testing <<
Tactical vs. Strategic Thinking in Penetration Testing
The tactical approach—compliance-driven, one-off vulnerability remediation—is like winning the battle. You should be designing your program to eliminate the root cause of these vulnerabilities, so you can save your team precious time and ensure your attack surface is fortified.
We recommend that organizations should use both tactical and strategic methods. Tactically, security teams can apply pentesting to identify exploitable vulnerabilities and fix them faster. This addresses the immediate, individual problem. Strategically, security leaders should focus on identifying the root causes that enable discovered vulnerabilities. Is there a problem in code development that’s introducing vulnerabilities? API endpoints exposed? Are cloud assets misconfigured? Does your credentials authentication process have holes? You need to identify the problem and fix it at the source.
The Synack Platform and Strategic Thinking
The Synack platform includes features that can help you to start thinking strategically and tactically. The platform encompasses five pillars of pentesting that form the core of a strategic approach to cybersecurity testing.
1) Vulnerability Management: Find and Manage Vulnerabilities that Matter
When organizations think of pentesting they often think only of discovery.What they should be thinking is a complete process from assignment of asset priority, to discovery of vulnerabilities, to reporting, patching and verification.
2) Operations and Support: The Synack Quality Promise
Synack operations teams ensure that remediation efforts concentrate on truly exploitable vulnerabilities by eliminating any false positives. Support teams are available to save your team time and deal with any questions or difficulties.
3) API and Integrations: Integrating Our Data with Yours for a Complete Picture
Vulnerability management is only one part, although a critical one, of a complete cybersecurity program. For a wider view of security testing and posture Synack has integrations with leading cybersecurity software, including Splunk, ServiceNow, KENNA and Microsoft Sentinel, Defender for Cloud and Azure DevOps.
4) Reporting and Real-time Analytics: Insights Into Your Strategic Security Posture
Pentesting only has value if it produces actionable results. Synack presents information you can use. You can see vulnerabilities by type in order to identify root causes (e.g. 80% of exploitable vulnerabilities are related to cross-site scripting), identify how rigorously an attack surface is tested with coverage analytics and understand how you measure up within your industry with the attacker resistance score.
5) Managed Community Access: On-demand Access to a Community of Expert Security Researchers
Synack manages an extensive community of highly-vetted security researchers with a variety of skills and expertise to satisfy individual testing requirements. Synack LaunchPoint controls and measures researcher and scanning activity to ensure coverage, spot trends, and control traffic.
Together, these five pillars can enable a risk-based approach that helps you accomplish your tactical and strategic goals.
Learn More
You can read more about Synack strategic thinking and the five pillars of the Synack platform in our new white paper, The Guide to Strategic Security Testing.




