Security should never be an afterthought when releasing a new application, updating source code, migrating resources to the cloud or doing anything else that might introduce new vulnerabilities into your organization’s attack surface. But security testing is often seen as an impediment to the pace of innovation and business.
It doesn’t have to be that way. Baking in control and visibility into security testing traffic can ensure you get the testing you want when you want it on target assets and can stop testing at any time. Fast paced innovation is also the culprit for your expanding attack surface with shadow IT, Internet of Things (IoT) and remote workers now a fact-of-life for security teams. You need testing coverage to know where testing gaps might exist on your network.
Why Synack Invests in Control and Visibility
What sets Synack apart from competition is our LaunchPointTM technology, which allows the Synack Red Team (SRT) to use hacking skills while delivering a traffic audit trail to clients. Synack also achieved the FedRAMP Moderate Authorized designation, enhancing data security in regions across the globe and providing Synack federal customers and all users with an added level of data protection.
These technologies provide an important building block for the Synack Platform. Similar to how you may think twice before getting in an untrackable, or unmarked cab, why would you conduct a pentest without assurances of full auditability?
“We know many of our customers are moving at a rapid pace and we want them to be empowered to have full control over testing activity. They need visibility into their testing activity to make strategic decisions and ensure full coverage of their attack surface,” said Synack’s co-founder and CTO, Mark Kuhr. “We don’t compromise when it comes to security controls”
The testing controls the Synack Platform provides helps you achieve full visibility, auditability and control.
Pause Assessment
Customer IT and security teams may have unforeseen internal events come up, or production systems impacted by testing. Synack makes it simple to pause testing for each assessment by way of a single button that can also be used to resume testing when the time is right.
Firewall Allowable IP Addresses
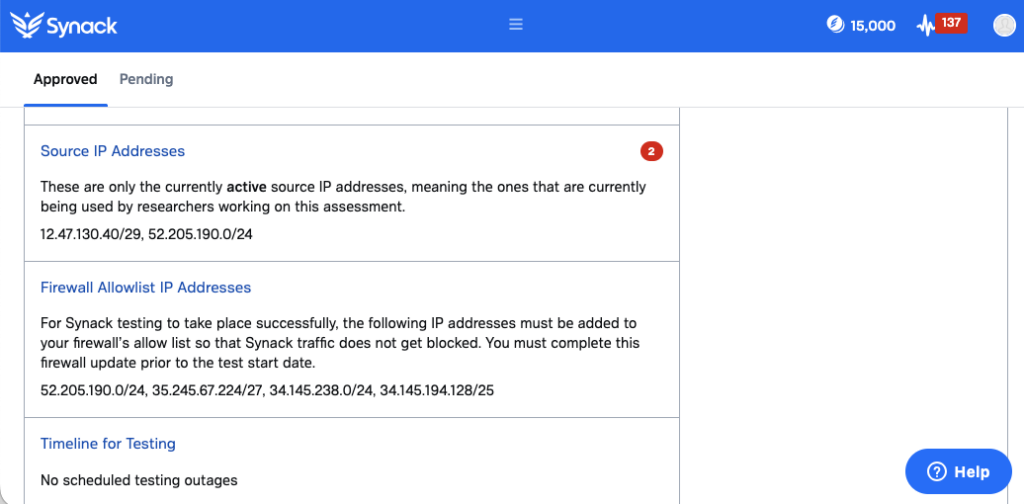
This feature provides a range of allowlist IP addresses, which clearly communicates to researchers what they’re allowed to test so they can easily assess the security of important targets and you can rest easy knowing they aren’t testing anything they aren’t supposed to.
Coverage Analytics that show what, when and how much has been tested
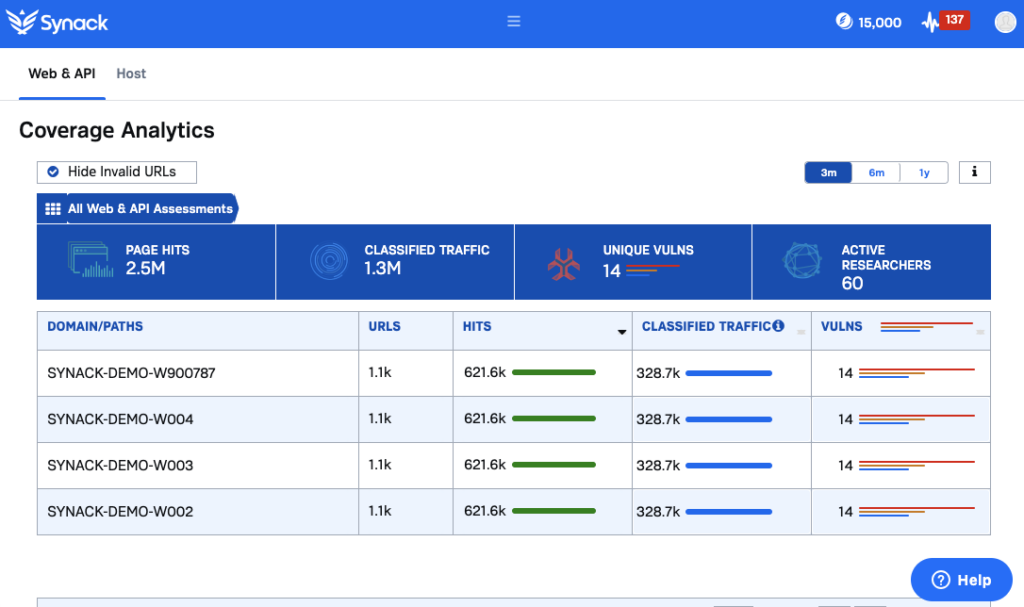
Most organizations view their pentesting through the lens of vulnerabilities found, but that is not a complete picture of a testing engagement. Testing coverage is arguably equally as important. Synack leverages testing traffic logs to provide real-time analytics on which domains, subdomains, API endpoints and IPs have been tested. All SRT hours are also tracked to assess researcher effort.
Synack Red Team Virtual Desktop Infrastructure
Testing can also cause concerns about where sensitive data and vulnerabilities are being stored. SRT security researchers use virtual desktop infrastructure (VDI) to test as an additional security control. Customers receive data protection during the exploit process and have the ability to cleanse data upon request. All SRT members are required to connect to their workspace before they start testing. Synack conducts full packet capture of all testing activity in order to show coverage to customers.
Keep Testing Secure So You Can Move Fast
Synack’s philosophy has always been to provide the SRT and our customers with the most secure pentesting option on the market, which is why we are continuously investing in features, technology, and processes to help protect our customers and researchers. This includes professional background checks for all researcher-applicants, single sign-on for more secure access to the Synack client portal, role-based access controls and continuous researcher vetting. You also have our support whenever you need a robust customer success team.
Synack’s commitment to our customers’ and researchers’ security is what sets us apart from traditional pentest and bug bounty options. Reach out for a demo.




