What I Could See and Do
Once I elevated myself to “manager” of a high-profile account, the platform opened the floodgates:
- Social media performance insights: engagement metrics, reach, trends, and upcoming campaign data.
- Commercial contracts: deals and financial figures for campaigns.
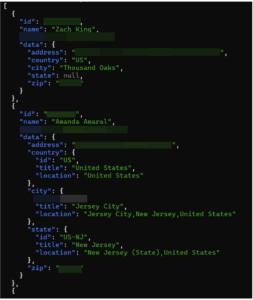
- Full addresses and sensitive location info: private addresses for individuals.
- Payment details: linked accounts, with the ability to alter payout settings.
- Unreleased material: videos, advertisements, and creative assets not yet made public.
It was a high-impact access control failure affecting some of the most influential people and organizations in the world including politicians, celebrities, content creators, influencers, and brands with billions in revenue.
Why This Was So Dangerous
The risks were staggering:
- A malicious actor could leak unreleased content, undermining major marketing campaigns.
- They could divert payments from celebrities or multinational brands.
- Exposure of personal addresses could lead to real-world safety risks.
- Manipulating metrics could skew critical business and brand decisions, potentially costing millions.
- It was a high-impact access control vulnerability, affecting individuals and organizations at the very top of global influence.
The Technical Flaw
The vulnerability came down to broken access control in the platform’s creator management workflow. In practice, it could be reproduced in a few simple steps:
- Select any high-profile account and send an invite to the manager’s roster.
- In the email input that appears, enter your own email address and submit.
- Check your inbox for the invitation and open the link in a different browser.
- Sign up or log in via that invitation, and suddenly, you are listed as a manager for that account.
The problem was that the platform failed to validate whether the requester was authorized to invite themselves as a manager. A simple invitation flow, intended to safely add trusted team members, could be abused to gain manager-level access to any account. This flaw was a classic case of broken access control: the platform’s “Send Invite” feature was supposed to let trusted team members manage accounts only after the invited account accepted the request, but it didn’t actually check if the person sending the invite was authorized. It’s a reminder that every feature that grants access to sensitive accounts needs strict permission checks, skipping them, even on something that seems harmless, can put people, organizations, and sensitive data at serious risk.