BENEFITS
Achieve more than the usual benefits of bug bounty
Trust
Synack’s researchers are rigorously vetted through a five-step process. The Synack Red Team is an elite community you can trust. Additionally, virtual workspaces provide records of traffic and testing activity, which are readily available.
Control
You control where, how and when to start, stop or pause testing with the push of button. Real-time updates are included within the Synack Platform.
Quality
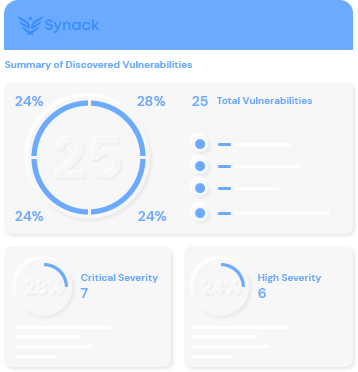
Thousands of bug bounty hunters of varying expertise generate noisy results of varying quality. Get highly skilled researchers to reveal only exploitable vulnerabilities so no time is wasted.
Features
1
Researcher Communication
2
Reporting and Coverage Analytics
3
Triaged Vulnerability Submissions by Synack Operations
FAQ