Synack has just released a new version of our security testing app for Splunk, which adds the full strategic value offered by Synack’s offensive security data to the defensive security monitoring which organizations already use in Splunk.
Splunk, a vendor used by many organizations as part of their security operations process, excels at gathering alerts, logs, events and other sources of security data. This gives security teams the ability to search and visualize data to find items of security concern.
The data is typically defensive in nature, from security monitoring tools such as vulnerability scanners, firewalls and endpoints. Analysis of this data is reactive, identifying what has already happened. Such analysis is important, but wouldn’t it be even better to also find exploitable vulnerabilities before bad actors do?
Synack provides strategic security testing that goes beyond passive scanning to proactively test for the presence of exploitable vulnerabilities in a safe and controlled way. Synack’s network of expert security researchers, known as the Synack Red Team (SRT), will “attack” an organization’s assets, providing detailed reports of the vulnerabilities that a real threat actor could exploit if left unpatched.
With specific recommendations to close security gaps security teams can address vulnerabilities and request a re-test to verify the vulnerabilities can no longer be exploited. The SRT act like a practice squad, continuously probing defenses for weaknesses.
Combining Blue and Red Team Data
In the past, security testing data typically has been siloed within specialized groups such as security red teams, and not made an integral part of organizations day to day security operations. By exposing, visualizing, and continuously updating offensive security testing in Splunk, organizations can find and fix more security gaps before bad actors do.
Results of security tests can also be searched alongside production security monitoring data to identify instances where threats are already present, and recommendations from Synack tests can provide security blue teams an immediate path to remediation.
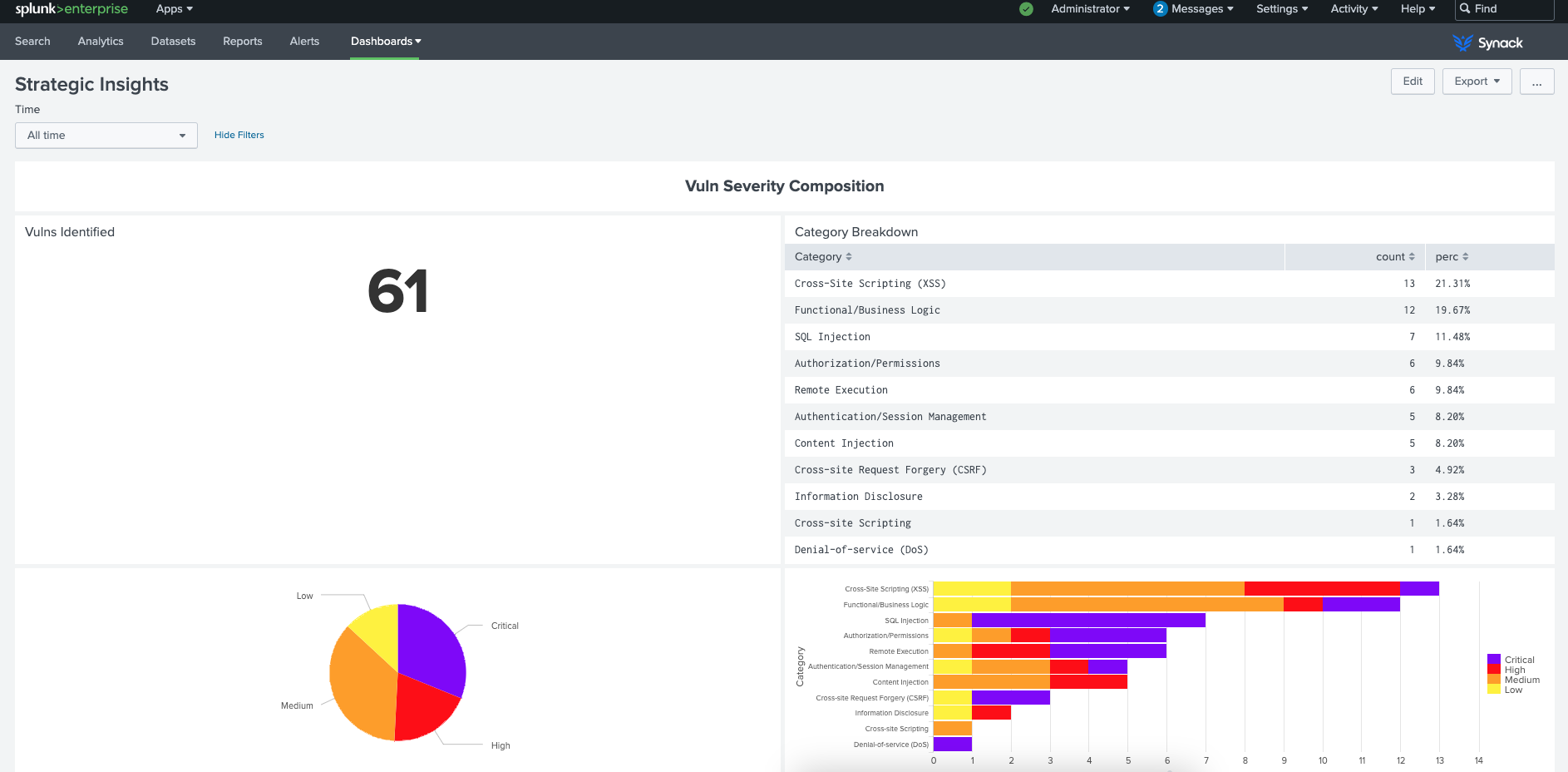
Using Splunk to analyze security testing data offers benefits, compared to looking at results in the Synack tool directly. For example, the Synack App for Splunk makes it easy to filter and pivot results of vulnerabilities by category, severity, impact and breadth. It’s not just CVE numbers that get reported but also a detailed report of what was tested, how the security researchers were able to breach the defense, and what specifically they recommend be done to stop someone else from exploiting the vulnerability.
So if a CISO asks whether a particular exploit has been tested, the answer can be found quickly and the full context and recommendation details are provided at the same time.
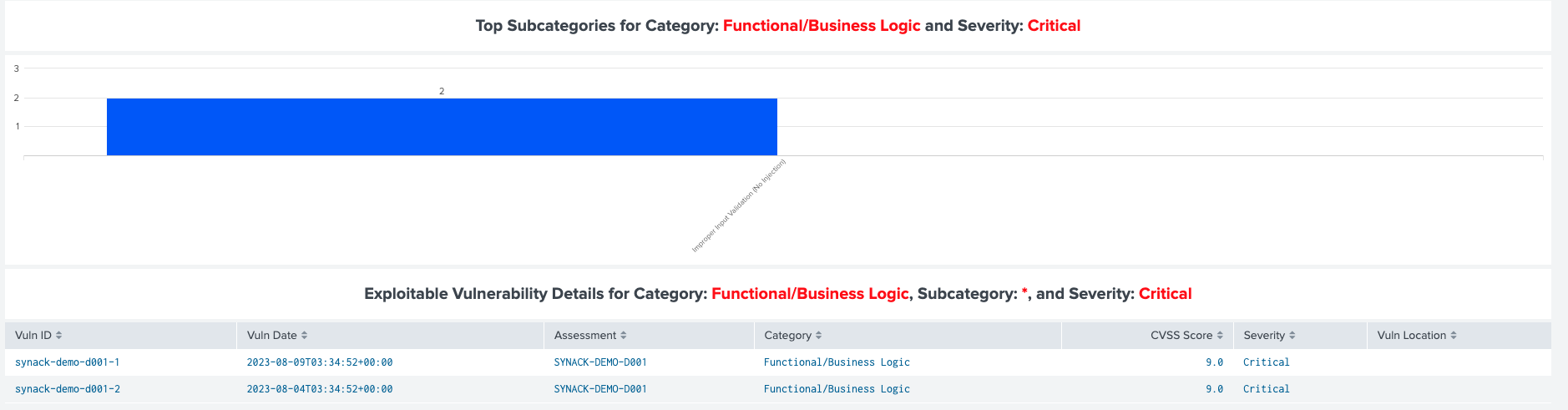
But every CISO has been burned by a security gap that was previously identified but never fixed. So as a follow up, the Synack App for Splunk offers a set of metrics such as number of days to remediation and patch efficacy to allow SecOps team to prove that security gaps have been addressed.
As with the other Synack security testing data, Splunk’s ability to search and pivot based on category, severity and area of impact makes analysis of security testing data faster and more effective. The Synack App for Splunk provides a rich set of pre-built dashboards to make security testing reporting visually compelling and easy to understand.
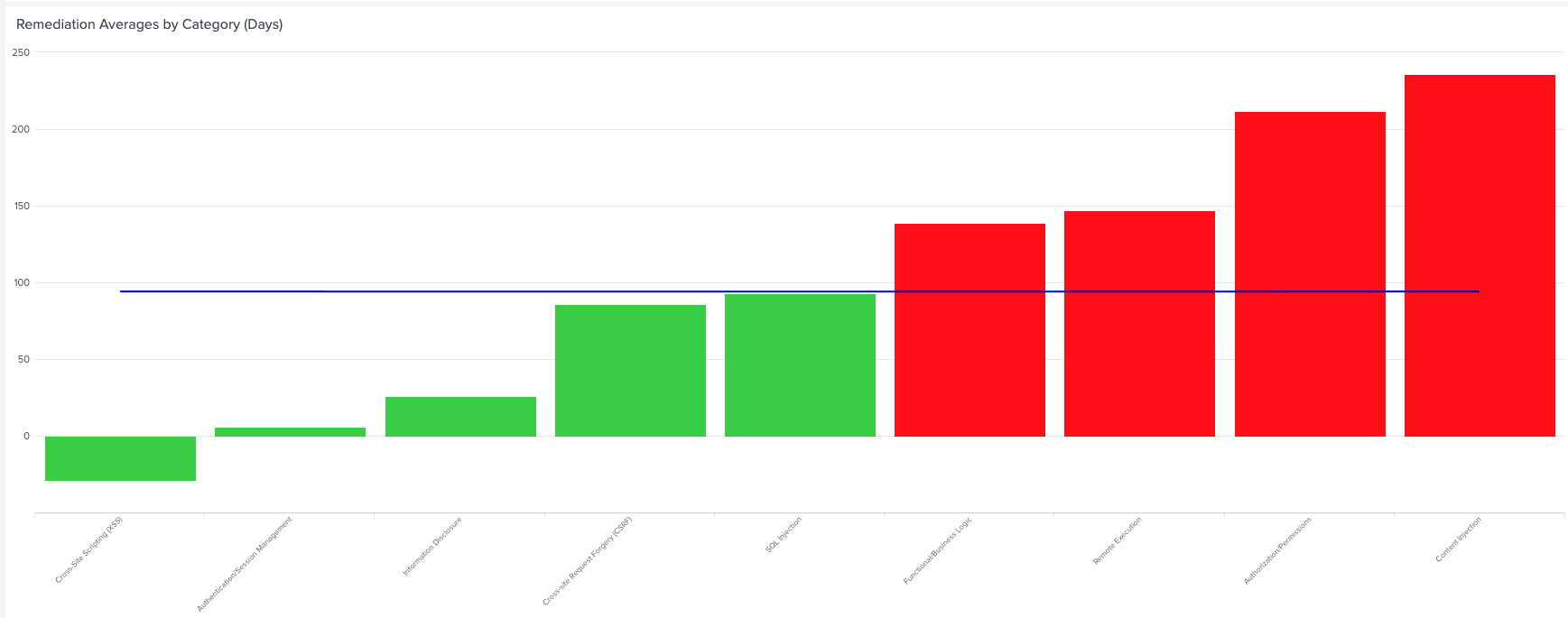
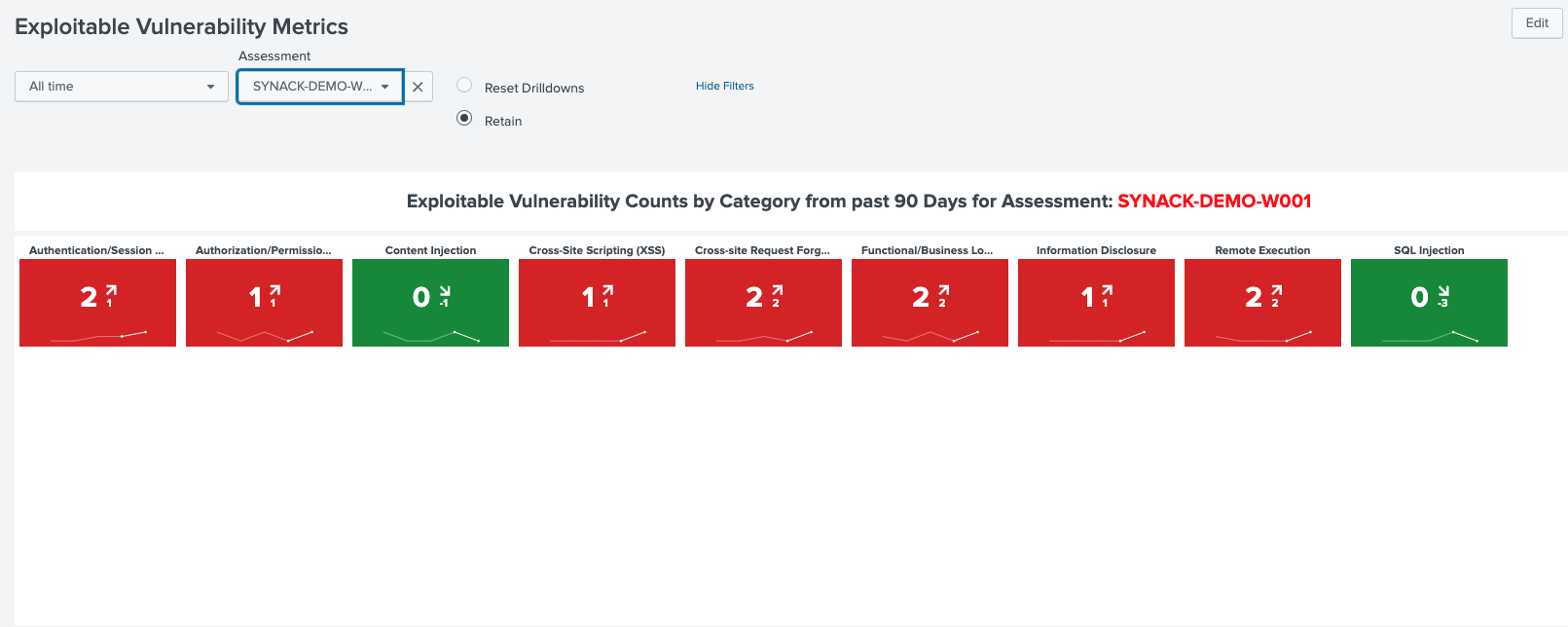
Lastly, the Synack App for Splunk provides filterable and searchable trending analyses to see whether different types of vulnerabilities are on the rise or decline, offering guidance about which areas security operations warrant more attention.
The new and improved version of the Synack App for Splunk is available free of charge – for use by existing Splunk and Synack customers – and can be downloaded from Splunkbase. We invite you to see for yourself the benefits of leveraging Synack’s strategic security testing data in a Splunk security operations environment.
If you’re a Splunk user, contact us for a demo to see how Synack integrates with Splunk.




