Hollywood portrays the mergers and acquisitions (M&A) process as people in expensive clothes sipping whiskey, trading insults and negotiating terms on a handshake deal. The reality is far more complicated—and takes significantly longer.
Cybersecurity can’t be an afterthought for organizations looking to advance past due diligence. While it would be ideal for all companies to care about their security, it’s crucial for potential M&A targets—or for companies angling to be acquired themselves.
“Undiscovered cyber risks can significantly diminish the value of the deal or, worse, lead to post-acquisition crises that more thorough due diligence might have prevented,” Thomson Reuters Westlaw Today experts said in a series on cybersecurity’s role in the M&A process. “Failing to adequately identify and address cybersecurity risks can result in substantial financial losses, legal repercussions, and irreparable reputational damage for both sides.”
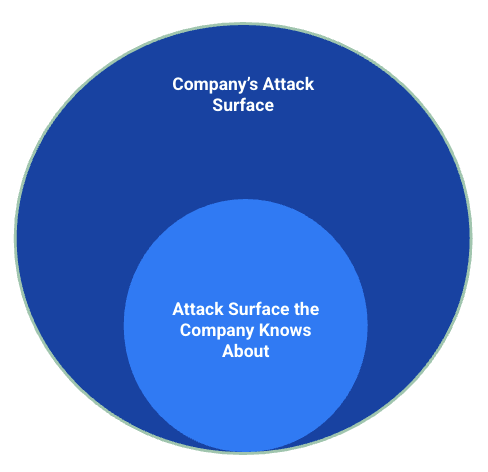
Implementing a robust security program the moment an executive announces due diligence to begin on an important deal is beyond the scope of this article. Godspeed to anyone tasked with that project. A more proactive approach is required, and in many cases, that starts with organizations realizing just how large their external attack surface truly is.
Starting with Open Source Intelligence
It’s not uncommon for organizations to rely on automated scanning tools for their attack surface discovery needs. These offerings certainly have their benefits (especially as they find ways to improve their capabilities with artificial intelligence), but they also have downsides. They’re often noisy, lack nuance and can miss things a cybersecurity professional would have noticed.
Enter Synack: We combine our proprietary attack surface discovery with open-source intelligence (OSINT) to help companies gain a clearer understanding of their external attack surface—through the lens of an attacker in ways that automated scanners simply cannot. Our goal isn’t to give organizations a haystack but to figure out where the needles are.
Attackers use the same process to discover weaknesses in a potential victim’s defenses. By operating with an adversarial mindset, Synack can help organizations determine the size of their attack surface and contextualize which mission-critical assets may need in-depth testing, and which may not need urgent attention.
OSINT 🤝 PTaaS
Attack surface discovery is just one aspect of Synack’s comprehensive penetration testing as a service platform. We can also help organizations identify the vulnerabilities most likely to be exploited by malicious hackers and determine whether efforts to mitigate those risks are likely to solve the underlying problems associated with them.
“Ensuring regulatory compliance, demonstrating a strong culture of security, and establishing a stable foundation for post-acquisition integration remain critical steps for success,” Westlaw Today’s experts said. “As the cyber landscape continues to evolve, staying vigilant and adaptable is key to managing the complexities of M&A transactions in the digital age.”
In other words: The M&A process is complex and comprehensive in ways that even a four-hour Martin Scorsese flick can’t do justice. What works for the silver screen doesn’t work in real life, which is why Penetration Testing as a Service (PTaaS) is the gold standard for companies looking to make it through due diligence relatively unscathed, at least as far as their security and compliance programs are concerned. Expensive clothes and whiskey optional!